- Aircrack Ng File To Crack Specified
- Aircrack No File To Crack Specified Key
- Aircrack No File To Crack Specified 64-bit
We all know we can use aircrack-ng to run a wordlist attack to crack WPA/WPA2, in this article I’m going to show you how to do the same using a tool called HashCat, and compare its speed with aircrack-ng.
The advantage of using HashCat is unlike aircrack-ng which uses the CPU to crack the key, HashCat uses the GPU, this makes the cracking process MUCH faster (results below).
Installing & using Hashcat
Invoking aircrack-ng with some arguments but without a file to crack causes a segmentation fault: Program received signal SIGSEGV, Segmentation fault. 0x00007ffff775bbfe in strcmpavx2 from /usr/lib/libc.so.6 (gdb) bt #0 0x00007ffff775bbfe in strcmpavx2 from /usr/lib/libc.so.6. Capture1 — name of the pcap file that will be generated, the pcap will be saved in the current working direcory where the command was run at unless the path is specified. –bssid — specifies the bssid of the WiFi you wish to crack its passwords. –channel — specifies the channel to listen on.
- First you need to download Hashcat from https://hashcat.net/hashcat/
- Navigate to the location where you downloaded it, and unzip it, personally I like to use 7zip.
- Open the Command Prompt (go to windows search and type cmd).
- Navigate to your Hashcat folder where it’s unzipped.
- Type hashcat32.exe or hashcat64.exe depending on the architecture of your CPU.
- In order to use the GPU, you need to get its id using the following command
mine is #3. Then you need to use the hash type which is 2500 for WPA, I do recommend using
to get familiar with the tool.
To specify device use the -d argument and the number of your GPU.
The command should look like this in end
Example:
Where Handshake.hccapx is my handshake file, and eithdigit.txt is my wordlist, you need to convert cap file to hccapx using https://hashcat.net/cap2hccapx/
Results:
Test1: Using HashCat, with Asus GTX 1080 OC edition which has GPU Boost Clock with 1936 MHz, total GB ram of 8 Gigabytes, and Cuda cores 2560.
CUDA = Computing performance Boost Clock = Increases the Clock speed.

Hashcat took 4 mins, 45secs to reach the end of the wordlist and crack the handshake with a wordlist of 100,000,000 passwords.
Test 2:Using Aircrack-ng on Kali installed as main operating system with is i7-7700k CPU – base clock of 4.20, turbo clock 4.50Ghz with 4 cores and 8 threads, it would take 4 hours 22 minutes 14 seconds try all the passwords in the wordlist.
Test 3: Kali installed as a virtual machine, in this case it would take 11 hours, 31 minutes and 40 seconds to try all passwords in the wordlist!
Resources:
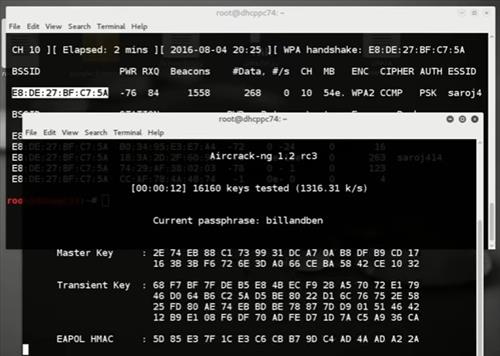
Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK key cracking program.
Aircrack-ng can recover the WEP key once enough encrypted packets have been captured with airodump-ng. This part of the aircrack-ng suite determines the WEP key using two fundamental methods. The first method is via the PTW approach (Pyshkin, Tews, Weinmann). The default cracking method is PTW. This is done in two phases. In the first phase, aircrack-ng only uses ARP packets. If the key is not found, then it uses all the packets in the capture. Please remember that not all packets can be used for the PTW method. This Tutorial: Packets Supported for the PTW Attack page provides details. An important limitation is that the PTW attack currently can only crack 40 and 104 bit WEP keys. The main advantage of the PTW approach is that very few data packets are required to crack the WEP key.
Aircrack Ng File To Crack Specified

The other, older method is the FMS/KoreK method. The FMS/KoreK method incorporates various statistical attacks to discover the WEP key and uses these in combination with brute forcing. It requires more packets than PTW, but on the other hand is able to recover the passphrase when PTW sometimes fail.
Additionally, the program offers a dictionary method for determining the WEP key.
For cracking WPA/WPA2 pre-shared keys, only a dictionary method is used. A “four-way handshake” is required as input. For WPA handshakes, a full handshake is composed of four packets. However, aircrack-ng is able to work successfully with just 2 packets. EAPOL packets (2 and 3) or packets (3 and 4) are considered a full handshake.

Aircrack No File To Crack Specified Key
Aircrack No File To Crack Specified 64-bit
SSE2, AVX, AVX2, and AVX512 support is included to dramatically speed up WPA/WPA2 key processing. With the exception of AVX512, all other instructions are built-in Aircrack-ng, and it will automatically select the fastest available for the CPU. For non-x86 CPUs, SIMD improvements are present as well.